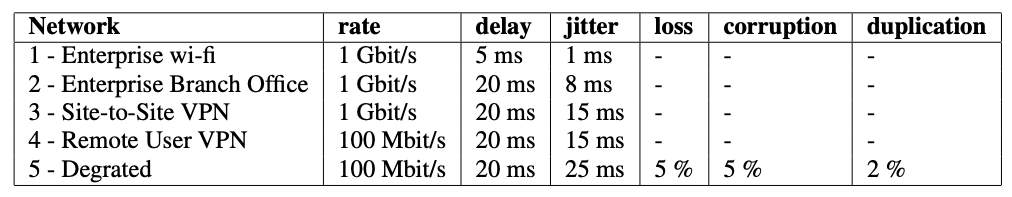
Parameters of the network scenarios
The USB-IDS-TC dataset was conceived to explore the dependence of ML/DL-based NIDS on the network used to collect the training traffic data. In this dataset, DoS attacks have been conducted in different network scenarios, in the belief that the network has a non-negligible effect on the detection capability of the NIDS as indicated by our initial analysis. Differently from existing datasets that collect the data in a single scenario, USB-IDS-TC allows studying the dependence of the attacks, traffic features and ML/DL models on the network.
USB-IDS-TC is released in the form of five csv files, where each file provides normal and DoS flow records of one network scenario in the following Table. Each csv file provides ready-to-use labeled network flows, obtained appending five previously-labeled flow collections (NOR - normal traffic, DoS attacks: HLK (hulk), GSL (slowloris), HSL (slowhttptest in slowloris mode) and HSP slowhttptest in slow POST mode).
The USB-IDS-TC dataset has been updated on 9th January 2026. The following files are the new version of the network captures on the five network scenarios. The old version is still available (here). It is interesting to discuss the reasons for this update; the details are presented here.

Parameters of the network scenarios
Along with the five original networks, in the new version of the dataset three additional scenarios have been considered, as shown in the following table.
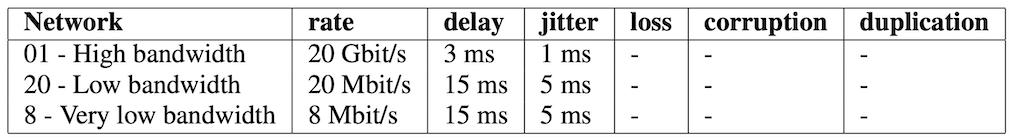
Parameters of the additional network scenarios
The captures are the following:
All the above files are freely downloadable for research use. Credits should be given to the developers by mentioning the source and referencing the dataset presentation paper shown on the home page of this site.
Free AI Website Maker